
Understanding API Authentication: A Guide to Cookie-Based,jwt
Understanding API Authentication: A Guide to Cookie-Based, Token-Based, and Basic Authentication,jwt
Introduction:
API authentication is a necessary thing of net improvement that ensures information safety and restricts unauthorized get entry to to included resources. There are quite a number authentication strategies available, and in this article, we will discover three frequent ones: Cookie-Based Authentication, Token-Based Authentication, Basic Authentication and JWT Token. By the cease of this article, you will have a clear grasp of how these techniques work and how to put in force them effectively.
1. Cookie-Based Authentication:
Cookie-Based Authentication is a common approach used to authenticate customers on the web. It depends on HTTP cookies to keep session records between the consumer and the server. When a consumer logs in, the server creates a special session identifier (cookie) and sends it to the client, which shops it in its memory. For each subsequent request, the patron sends this cookie lower back to the server, permitting the server to pick out and authenticate the user.
Real-World Example:
Let's reflect on consideration on a easy net software the place customers want to log in to get entry to their profile page. Upon profitable login, the server generates session cookie with a special session ID and units it in the HTTP response
Request:

POST /login HTTP/1.1
Host: example.com
Content-Type: application/json
{"username": "test", "password": "test1"}
Response:

HTTP/1.1 2 hundred O Set-Cookie: sessionID=abcd1234; Path=/
Subsequent requests to get admission to covered sources will encompass the cookie:
Request:
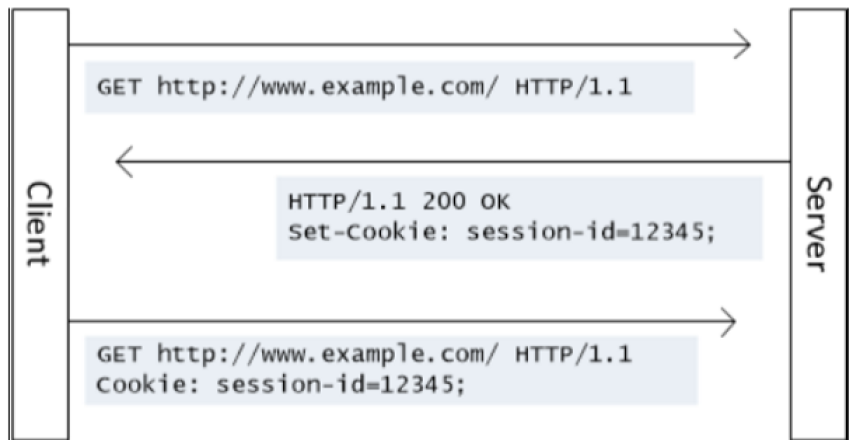
GET /profile HTTP/1.1 Host: example.com Cookie: sessionID=1234
Response:
2 Basic Authentication:
Basic Authentication is a easy token-based technique the place the customer sends a username and password in the request headers, Base64 encoded. The server verifies the credentials and responds with the requested data.
Real-World Example:
Consider an API that offers get admission to to person statistics the usage of Basic Authentication.
Request:

GET /api/user HTTP/1.1 Host: example-api.com Authorization: Basic dXNlcjE6cGFzc3dvcmQxMjM=
Response:

HTTP/1.1 200 OK
Content-Type: application/json
{"username": "test", "email": "[email protected]", "role": "test"}
3 JSON Web Tokens (JWT):
JWT is a famous token-based authentication technique that encodes person data in a invulnerable and compact manner. The server symptoms the JWT, making sure its authenticity.
Real-World Example:
In this scenario, the user interacts with a web or mobile application that communicates with the server via API calls. To ensure secure authentication, the server uses JSON Web Tokens (JWT) for the process.
User Log-in Request:
When the user attempts to log in, the application sends a log-in request to the server. The request includes the user's credentials, such as their username and password.
Request:

POST /api/login HTTP/1.1
Host: example-api.com
Content-Type: application/json
{
"username": "user123",
"password": "password123"
}
Server Authentication:
Upon receiving the log-in request, the server authenticates the user's credentials. If the credentials are valid, the server generates a JWT token for the user.
JWT Token Generation:
The JWT token is a JSON object containing three parts: the header, the payload, and the signature. It is then signed using a secret key known only to the server, ensuring its authenticity.
Example JWT Token (not actual token):
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InVzZXIxMjMiLCJpYXQiOjE2Mjg4MzI4MjEsImV4cCI6MTYyODg0NjgyMX0.mwMhzX3kzH_qxMGwVmq2Q3vdV7c79npKfBYV9udJKsM
Token Sent in Response:
The server sends the generated JWT token as part of the response to the log-in request.
Response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InVzZXIxMjMiLCJpYXQiOjE2Mjg4MzI4MjEsImV4cCI6MTYyODg0NjgyMX0.mwMhzX3kzH_qxMGwVmq2Q3vdV7c79npKfBYV9udJKsM"
}
Subsequent Requests with JWT Token:
After receiving the JWT token, the application stores it securely, typically in local storage or a cookie. For each subsequent API request that requires authentication, the application includes the JWT token in the request headers.
Request:
GET /api/profile HTTP/1.1 Host: example-api.com Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InVzZXIxMjMiLCJpYXQiOjE2Mjg4MzI4MjEsImV4cCI6MTYyODg0NjgyMX0.mwMhzX3kzH_qxMGwVmq2Q3vdV7c79npKfBYV9udJKsM
Server Authentication and Response:
The server verifies the JWT token's signature and decodes the payload to identify the user. If the token is valid and not expired, the server processes the request and sends back the requested data.
Response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"username": "user123",
"email": "[email protected]",
"age": 30
}
By using JWT token authentication, the API ensures secure log-ins, allowing users to access their accounts and protected resources efficiently and with reduced security risks.
Conclusion:
API Authentication is a vital issue of cutting-edge net development. In this article, we explored three standard methods: Cookie-Based Authentication, Token-Based Authentication (Basic Authentication, Access Tokens, and JSON Web Tokens). Each approach has its advantages, and the preference relies upon on the precise necessities of your application. By the use of real-world examples, we hope to have supplied you with a clearer perception of how these authentication techniques work and how they can be carried out in your projects.





